WordPress website server attacked using xmlrpc.php
Having your WordPress website get hacked is no fun at all, especially when you find out it’s being used to attack other websites. But that’s exactly what happened recently to a client of ours.
The issue came about with the xmlrpc.php file used by WordPress plug-ins such as Jetpack. The vulnerable file can be altered to ping other websites, using your server, in a distributed-denial-of-service (DDoS) attack.
If your server appears to have an unexpected heavy load (meaning, the site is not experiencing excessive incoming traffic, pushing large amounts of video, or performing other processer-intensive tasks), it’s possible it is being used as a bot to attack other websites.
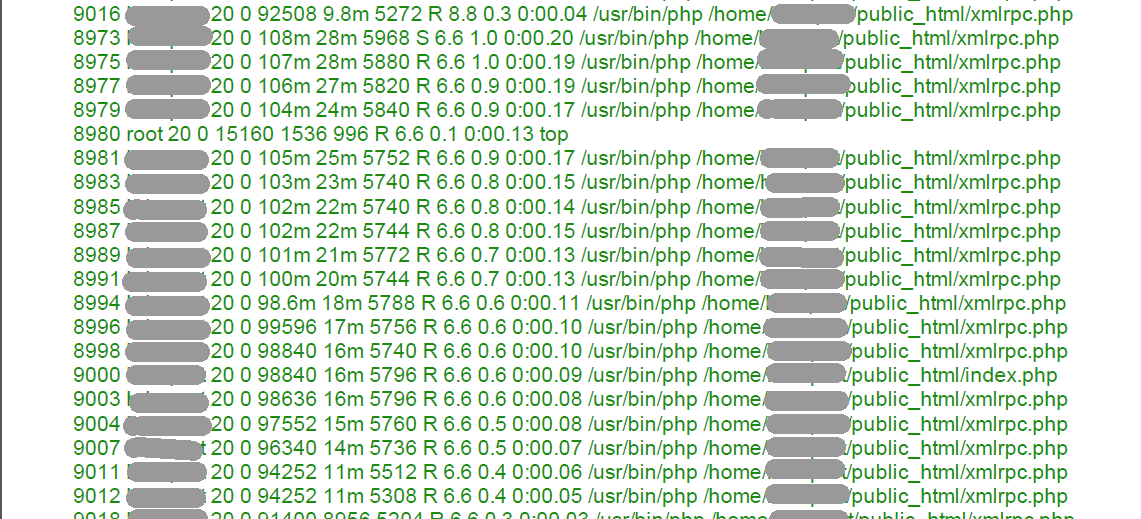
In this particular case the xmlrpc.php file, stored at the root folder of the website domain (not the root of the server), had several lines of code that were not supposed to be there. The code instructed the website to ping other websites (see graphic showing a screenshot of log entries), and for some reason started doing its work excessively before the WHM (Web Host Manager) software sent warnings about memory problems.
The xmlrpc.php file, strangely enough, showed up as last being modified in 2012. But it was probably an earlier version of xmlrpc.php – most likely the 1.1 version issued in 2009.
The solution? You can remove or disable the xmlrpc.php file. Then, look in your current logs to see if there are still outgoing pings. Keep in mind, however, that the file may be used by a plug-in on your site for trackbacks. Do the plug-in developer a favor and mention the exploit in the WordPress plug-in community.
Another solution is to block the file using .htaccess. You might also update to the latest version of xmlrpc.php if compatible. Here’s some info on the versions.
Finally, a more tedious method would be block all the IPs that are utilizing the file, but you may find yourself having to maintain those “blacklist” IPs. See the links below for further instruction.
WordPress is not the only CMS platform affected by the xmlrpc.php exploit; Drupal, Joomla, and vBulletin are also targets.
Here’s a more detailed article about WordPress being used for DDoS attacks, and here’s one from the same author distinguishing DDoS from Brute force attacks.